There is one thing that make us so vulnerable is ignorance. Today, everything is going to be depended on the internet. Yes, and you know it better! and a concept that we use to secure our internet accounts and all is our passwords. but is it enough to set password and feel that we are secure? are you really aware about of how to use passwords?
Our lack of understanding about passwords is allowing crooks to spy on us, steal from us, and deceive us into thinking nothing ever happened. Despite the volumes of texts that have already been written about them, how many of us have ever read a single chapter paragraph about the nitty-gritty of passwords?
That’s why i have compiled the following three short lists which outline the most common misconceptions about passwords; the ways in which our passwords can be stolen; and the tools you need to make sure it doesn’t happen to you.
Each of these sections can be read in less than two minutes. But once you’re done, you will have acquired enough information to deal safely and confidently with your passwords.
Password Myths You Should Stop Believing
1. A file, folder, computer, or account protected by a password is safe.
Read the rest of the article and learn why that statement is no longer true.
2. Your passwords are secure as long as you only deal with reputable online businesses.
Major online businesses that serve tens of millions of customers worldwide are expected to hold a treasure trove of personal information – the favorite diet of identity thieves. Therefore, these companies are always in the crosshairs of the world’s most highly-skilled hackers.
Take these recent examples, for instance:
- LinkedIn – A file with 6.5 million passwords from LinkedIn accounts appeared in an online forum based in Russia.
- Yahoo – 450,000 usernames and passwords from Yahoo! were posted online
- Sony (Playstation) – This massive breach involved 77 million Sony Playstation user accounts containing passwords and other personal information.
Reputable businesses like LinkedIn, Yahoo! and Sony should be implementing the strongest security countermeasures available. But even these are not strong enough to withstand attacks all the time…
3. A password input box that obscures characters as you type hides your password from prying eyes.
The dots or asterisks displayed on a password input box are just meant to prevent people near you from seeing what you’re entering in there. How the password is actually stored or sent is a different story.
4. “Strong” passwords are difficult to compromise.
Even if your password is long and complex (e.g. a combination of uppercase and lowercase letters, numbers and other non-alphanumeric characters), if it is stored or sent in plaintext, you’re toast if the hackers get hold of it.
Plaintext means it can be viewed exactly the way it has been entered, using easily accessible tools. For example, if your password is Super$ecretp@Ss, a free downloadable tool like Ettercap enables your password to be viewed exactly in that form: Super$ecretp@Ss.
If, however, your password is encrypted, it means that it has been scrambled; it cannot be viewed using the same tool (Ettercap). It might be displayed something like this: xt%y&1sm^*gt;>2.
Unfortunately, many software applications still store and send passwords in plaintext. That is why hackers still find the first three items in the next section so effective.
5. Hackers use sophisticated tools to steal your password.
Actually, many successful hackers don’t require sophisticated tools to acquire passwords. Some simply use crafty conversational skills. In the highly publicised hacking of Wired Senior Writer Mat Honan, the hackers made extensive use of social engineering, a technique that relies heavily on the art of deception. More about this shortly.
In the meantime, let’s talk about how crooks can get a hold of your passwords.
Commonly Used Techniques for Stealing Passwords
1. Hacking into a server that stores passwords in plaintext
There are many ways to do this. I won’t delve into the technical details but they can range from sophisticated-sounding methods like an ‘SQL injection’ to “manual” methods like stealing the server’s hard disk.
Once the attacker gets into the system, passwords can be easily retrieved from the database because they are all in plaintext (as previously explained).
Considering the risks of storing sensitive data in plaintext, you’d think it would be unimaginable for big companies to store passwords in this manner. Well, think again. That’s exactly what Yahoo! did, which led to that massive data breach referred to earlier.
2. Operating as a man-in-the-middle
In a man-in-the-middle (MITM) attack, an attacker hijacks communications between two machines (e.g. a server and a client, two clients, a router and a client, or a router and a server). He then sets up his computer to impersonate both legitimate machines and then makes it appear they are still communicating with one another.
As a result, all of their messages would pass through his computer, allowing him to view any information that is sent in plaintext; including usernames and passwords.
3. Luring gullible victims using trojans
Trojans are malware, disguised as downloadable programs, that hackers make available through harmless-looking emails or websites. That interesting downloadable freebie online, for example, might be a trojan…
Once downloaded, a trojan can stealthily perform whatever nefarious activity it is programmed to do. One common activity is recording keyboard strokes (keylogging), whenever the victim logs in to a “secure” site; another is scanning the memory and extracting what it suspects to be passwords (“memory dumping”). When done, the malware transmits this information to the attacker.
4. Employing social engineering
As mentioned earlier, this technique does not require any sophisticated hacking tool.
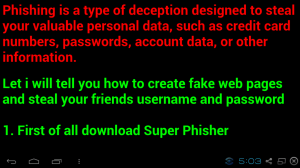
A commonly used social engineering trick (known as “phishing”) involves sending out fake notification emails informing users of a data breach at a legitimate website where the users have accounts. The email would then instruct the users to reset their passwords by clicking on a link that takes them to a spoofed website, closely resembling the real one.
The fake page asks the users to enter their username, old password, and new password. Those falling for that then pass their login credentials into the wrong hands.
Another example of social engineering is simply calling a company’s tech support, convincing them you’re someone else, asking for a password reset, and then requesting that the temporary password be sent to an email address you control.
5. Using brute force
Do you know what the crudest way of cracking a password is? Simple. You just make an educated guess.
You can base your guess on the user’s name and a bunch of dates important to him (e.g. his birthday or wedding day). If your first guess doesn’t work, you guess again. And again. And again. Until you get it correctly. Some systems don’t put a limit to the number of times you can enter a password.
Of course, this can take forever… unless you can automate the process.
Brute force attack programs like John the Ripper, Cain & Abel, or TCH Hydra, enable you to do just that. These programs can make a large number of rapid intelligent guesses…which is great for hackers, but not so great for the security of your passwords.
Now that you’re familiar with the common techniques used for stealing passwords, let’s take a look at what tools you can use to foil them.
Must-Have Tools for Maintaining Password Security
If hackers use tools to simplify and automate their exploits, then you should have your own tools to make it more difficult for them.
One thing to keep in mind when choosing a security tool, especially if you’re going to let other people use it, is that it should be easy to use, as well as providing the necessary level of security.
Once a security mechanism or tool is too sophisticated, end users will tend to avoid it. This will make you vulnerable again, and the time and money you invested into it will essentially go to waste.
Keeping that in mind, consider acquiring these tools:
A Password Generator – this helps you create passwords; especially handy if you’re tired of composing your own, and if you need very strong passwords. Here’s a tool that allows you to generate both simple and strong passwords: makeagoodpassword.com
A Password Strength Tester – If you really want to compose your own passwords, you should make sure they’re strong enough. Tools like howsecureismypassword.net can help you determine whether your password is difficult to crack.
A Password Manager – This tool helps you securely manage all your passwords in one location and means you don’t have to remember multiple, complicated passwords. You can centralise all your passwords from your email accounts, blogs, social networking sites, online banks, and so on. Here’s a popular one that’s also free: KeePass
A Built-in Volume or Hard Disk Encryption – If you prefer to keep your passwords in files and save them in your desktop or laptop, the easiest way to secure them is to use your operating system’s built-in volume or hard disk encryption programs. Using them is pretty straightforward. In Windows, use BitLocker. And in Mac OS X, use FileVault.
An Encryption-Enabled Password Sharing Tool – When people send passwords to work colleagues they usually email them. However, many email services are vulnerable to man-in-the-middle attacks. Use a free tool like Firepass, which encrypts your password and sends it so that only the intended recipient can access it.
Just employing the above five tools will put you way ahead of the crowd; most people do not put enough thought into creating, storing or sending their passwords; it’s never too late to start getting serious about protecting your most confidential and sensitive information.